Network Deployment (Distributed operating systems), v8.0 > Reference > Custom properties
Core group bridge custom properties
Use these custom properties for advanced configurations for core groups and core groups that communicate with the core group bridge.
We can use the custom properties page to define the following core group bridge custom properties:
- CGB_ENABLE_602_FEATURES
- cgb.allowUndefinedBridges
- cgb.rebuild.waitTime
- FW_PASSIVE_MEMBER
- IBM_CS_LS_DATASTACK_MEG
CGB_ENABLE_602_FEATURES
 Deprecated feature: You should use the cgb.allowUndefinedBridges
custom property instead of the CGB_ENABLE_602_FEATURES custom proeprty.
The cgb.allowUndefinedBridges custom property performs the same functionality
as the CGB_ENABLE_602_FEATURES custom property performed in Versions
6.0.x and 6.1.x.
Deprecated feature: You should use the cgb.allowUndefinedBridges
custom property instead of the CGB_ENABLE_602_FEATURES custom proeprty.
The cgb.allowUndefinedBridges custom property performs the same functionality
as the CGB_ENABLE_602_FEATURES custom property performed in Versions
6.0.x and 6.1.x.
If we have automation that adds this property to your core group bridge settings, this automation still works in this version of the product. However you should update your automation to add the cgb.allowUndefinedBridges custom property instead of the CGB_ENABLE_602_FEATURES custom property because the CGB_ENABLE_602_FEATURES custom property might not be recognized as a valid property in future releases. depfeat
cgb.allowUndefinedBridges
We can define the cgb.allowUndefinedBridges custom property on all of the access point groups in the configuration if to have the capability to add core group bridge servers to the configuration without restarting the other servers in the configuration. After you enable this property, you can add a core group bridge server in one cell, without modifying the configuration in the other cell to include peer ports for the core group bridge server. The core group in the other cell automatically discovers the peer ports for the first cell when the first cell initiates communication with the second cell.
 For transitioning users: The cgb.allowUndefinedBridges
custom property performs the same functionality as the CGB_ENABLE_602_FEATURES
custom property performed in Versions 6.0.x and 6.1.x. If we have automation that adds this property to your core group bridge settings, this automation still works in this version of the product. However
you should update your automation to add the cgb.allowUndefinedBridges
custom property instead of the CGB_ENABLE_602_FEATURES custom property because the CGB_ENABLE_602_FEATURES custom property might not be recognized
as a valid property in future releases.trns
For transitioning users: The cgb.allowUndefinedBridges
custom property performs the same functionality as the CGB_ENABLE_602_FEATURES
custom property performed in Versions 6.0.x and 6.1.x. If we have automation that adds this property to your core group bridge settings, this automation still works in this version of the product. However
you should update your automation to add the cgb.allowUndefinedBridges
custom property instead of the CGB_ENABLE_602_FEATURES custom property because the CGB_ENABLE_602_FEATURES custom property might not be recognized
as a valid property in future releases.trns
The existence of the cgb.allowUndefinedBridges property automatically enables this property. Therefore, you can set the value to any string value. Setting the value to false does not disable the property.
To disable the property, remove it from the list of defined custom properties or change its name.
If you decide to use the cgb.allowUndefinedBridges custom property, decide which cell is the listener cell and which cell initiates communication with the other cells before you begin the configuration. The listener cell does not need to contain any peer access points or peer ports for the other cells in the configuration. For example, in a configuration that contains a secured cell and an unsecured cell, configure the unsecured cell as the listener. The unsecured cell cannot access information about the secured cell. Configure the core group bridge service on the listener cell first. Do not configure the cgb.allowUndefinedBridges custom property if we have already configured the FW_PASSIVE_MEMBER custom property. Any server for which the FW_PASSIVE_MEMBER custom property is configured cannot initiate contact with other systems in the configuration.
cgb.rebuild.waitTime
Use this property in a core group bridge configuration to specify, in seconds, the length of time that the core group bridge service waits for a core group bridge rebuild to complete.
This property is ignored unless we have specified the IBM_CS_HAM_PROTOCOL_VERSION=6.0.2.31 core group custom property for every core group that is part of the core group bridge configuration.
FW_PASSIVE_MEMBER
Use this property in a core group bridge configuration when there is a firewall between the core groups and the secure side of the firewall is configured to listen only.
Set the FW_PASSIVE_MEMBER custom property to make the bridge interfaces that are in the core group access point passive. Set the value on the core group access point that is on the secure side of the firewall so that the core group bridge interfaces listen for connections from the unsecured side of the firewall but do not initiate any connections. The servers on the secure side of the firewall are passive. The custom property should correspond to your defined firewall rules that allow connections from the unsecured region to the secure region only.
To configure this custom property, click...
Servers > Core Groups > Core group bridge settings > Access point groups > access_point_group_name > Core group access points > core_group_access_point_name > Show detail > Custom properties > New in the admin console.
You also must set this custom property in any peer access points that refer to the core group access points that you configure with this custom property.
Example
Figure 1. Configuring the FW_PASSIVE_MEMBER custom property 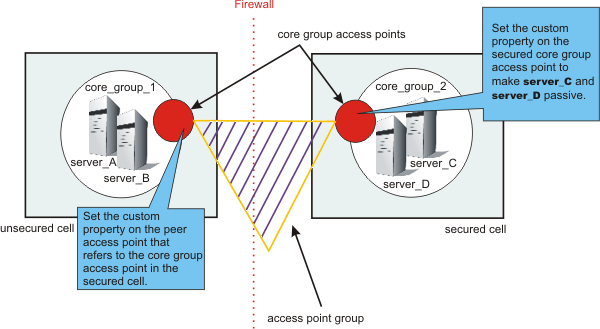
For example, server_A and server_B are configured in core_group_1. Server_C and server_D are configured in core_group_2. Core_group_2 is behind a firewall that is configured to listen only through the firewall. Core_group_1 is on the unsecured side of the firewall. Core_group_1 and core_group_2 can communicate with each other through an access point group.
To configure server_C and server_D to be passive, perform the following steps:
- In the admin console for the cell that contains core_group_2,
click...
Servers > Core Groups > Core group bridge settings > Access point groups > access_point_group_name > Core group access points > core_group_access_point_name > Show detail > Custom properties > New .
- Add the FW_PASSIVE_MEMBER custom property. Enter any value to enable the property.
- In the admin console for the cell that contains core_group_1,
click...
Servers > Core Groups > Core group bridge settings > Access point groups > access_point_group_name > Peer access points > peer_access_point_name > Show detail > Custom properties > New . The peer access point you select should correspond to the core group access point for core_group_2.
- Add the FW_PASSIVE_MEMBER custom property. Enter any value to enable the property.
By configuring the FW_PASSIVE_MEMBER custom property, you configured the servers on the secured side of the firewall, server_C and server_D, to be passive. These servers listen for connections from the other side of the firewall but do not initiate any connections to the unsecured side of the firewall.
IBM_CS_LS_DATASTACK_MEG
Use this custom property to eliminate a condition that is reported by a message that is displayed repeatedly in your SystemOut.log file.
New feature: Beginning in WAS v8.0 you can configure the server to use the HPEL log and trace infrastructure instead of using SystemOut.log , SystemErr.log, trace.log, and activity.log files or native z/OS logging facilities. If you are using HPEL, you can access all of your log and trace information using the LogViewer command-line tool from your server profile bin directory. See the information about using HPEL to troubleshoot applications for more information on using HPEL.New feature:
You might see a message similar to the following message in the SystemOut.log file multiple times:
[9/24/04 13:28:19:497 CDT] 00000013 VSync W DCSV2005W: DCS Stack DefaultAccessPointGroup.P at Member 172.16.1.86:9353: The amount of memory available for synchronization is low. The configured memory size is 418816 bytes. Currently used memory size is 420307 bytes.
If the member IP address is in the format of a dotted decimal IP address and port, you can eliminate these messages by increasing the amount of memory that is allocated to the core stack used for core group communication. Increase the value of this property until you no longer see the message in your SystemOut.log file. Because the memory is dynamically allocated, setting a larger stack size than you need does not cause memory problems.
Set the custom property on the bridge interface that contains the particular member that is in the messages. We can also set the custom property on the access point group or the core group access point. If you set the value on the access point group or core group access point, all the bridge interfaces that are in the particular group are affected. If you set the value on an individual bridge interface and an access point group or core group access point, the value that is set for the bridge interface is used. If the value is set on both an access point group and a core group access point, the value that is set for the core group access point is used.
To configure this custom property...
- Set the custom property in the admin console.
- To set the custom property on a bridge interface...
Servers > Core Groups > Core group bridge settings > Access point groups > access_point_group_name > Core group access points > core_group_access_point_name > Show detail > Bridge interfaces > bridge_interface_name > Custom properties > New .
- To set the custom property on a core group access point...
Servers > Core Groups > Core group bridge settings > Access point groups > access_point_group_name > Core group access points > core_group_access_point_name > Show detail > Custom properties > New .
- To set the custom property on an access point group...
Servers > Core Groups > Core group bridge settings > Access point groups > access_point_group_name > Show detail > Custom properties > New .
- To set the custom property on a bridge interface...
- Add the IBM_CS_LS_DATASTACK_MEG custom property. Enter a value that is greater than the default value of 5 megabytes.
| Units | megabytes |
| Default | 5 |
Configure the core group bridge service
Configure the core group bridge between core groups that are in different cells
Use HPEL to troubleshoot applications
Configure the core group bridge service