Apache HTTP Server Plug-In
Overview
The Apache HTTP Server Plug-In allows requests to be proxied from an Apache HTTP Server to WebLogic Server. The plug-in enhances an Apache installation by allowing WebLogic Server to handle requests that require the dynamic functionality of WebLogic Server.
The plug-in is intended for use in an environment where an Apache Server serves static pages, and another part of the document tree (dynamic pages best generated by HTTP Servlets or JavaServer Pages) is delegated to WebLogic Server, which may be operating in a different process, possibly on a different host. To the end user - the browser - the HTTP requests delegated to WebLogic Server still appear to be coming from the same source.
HTTP-tunneling, a technique which allows HTTP requests and responses access through a company's firewall, can also operate through the plug-in, providing non-browser clients access to WebLogic Server services.
The Apache HTTP Server Plug-In operates as an Apache module within an Apache HTTP Server. An Apache module is loaded by Apache Server at startup, and then certain HTTP requests are delegated to it. Apache modules are similar to HTTP servlets, except that an Apache module is written in code native to the platform.
You install the Apache HTTP Server Plug-In as an Apache module in your Apache HTTP Server installation. There are two ways that this module can be compiled and linked to Apache - as a statically linked module (available only for Apache version 1.3.x), or as a Dynamic Shared Object (DSO).
A DSO is compiled as a library that is dynamically loaded by the server at run time, and can be installed without recompiling Apache.
Install the Apache HTTP Server Plug-In as a Dynamic Shared Object
- Configure Apache 2.0.
Use the multi-threaded and single-process model, mpm_worker_module by including the option...
--with-mpm=worker
...when configuring the source tree
- The Apache plug-in is distributed as a shared object (.so) for AIX, Solaris, Linux, Windows, and HPUX11 platforms. BEA WebLogic supplies versions of shared object files that vary according to platform, whether or not SSL is to be used between the client and Apache, and the SSL encryption strength (regular or 128 bit - 128 bit versions are only installed if you install the 128 bit version of WebLogic Server).
Operating System Shared Object Location AIX WL_HOME/Server/lib/aix Solaris WL_HOME/Server/lib/solaris Linux WL_HOME/Server/lib/linux Windows (Apache 2.0 only) WL_HOME/Server/bin HPUX11 WL_HOME/Server/lib/hpux11 For Apache 2.0.x on HP-UX11, set the following environment variables BEFORE you build the Apache server. Because of a problem with the order in which linked libraries are loaded on HP-UX, a core dump can result if the load order is not preset as an environment variable before building.
export EXTRA_LDFLAGS="-lstd -lstream -lCsup -lm -lcl -ldld -lpthread"
- Choose the appropriate version of the plug-in shared object from the following table:
Apache Version Strength Encryption 128-bit Encryption Standard Apache Version 1.x mod_wl.so mod_wl128.so Apache w/ SSL/EAPI V1.x (Stronghold, modssl etc.)
mod_wl_ssl.so mod_wl128_ssl.so Apache + Raven V1.x Required because Raven applies frontpage patches that makes the plug-in incompatible with the standard shared object
mod_wl_ssl_raven.so mod_wl128_ssl_raven.so Standard Apache V2.x mod_wl_20.so mod_wl28_20.so - Locate the shared object directory for your platform
- Identify the plug-in shared object file for your version of Apache
- The Apache HTTP Server Plug-In will be installed in your Apache HTTP Server installation as an Apache Dynamic Shared Object (DSO), which is based on a module mod_so.c, which must be enabled before mod_wl.so is loaded. If you installed Apache HTTP Server using the script supplied by Apache, mod_so.c is already enabled.
To verify that mod_so.c is enabled...
APACHE_HOME/bin/httpd -l
This command lists all enabled modules. If mod_so.c is not listed, rebuild your Apache HTTP Server, making sure that the following options are configured:
--enable-module=so
--enable-rule=SHARED_CORE - Install the Apache HTTP Server Plug-In module.
- For Apache 1.x, use a command shell to navigate to the directory in your WebLogic Server installation that contains the shared object for your platform and activate the weblogic_module by issuing this command (note that have Perl installed to run this Perl script):
perl APACHE_HOME/bin/apxs -i -a -n weblogic mod_wl.so
This command copies the mod_wl.so file to...
APACHE_HOME/libexec.
...and adds two lines of instructions for weblogic_module to the httpd.conf file and activates the module. Make sure that the following lines were added to your APACHE_HOME/conf/httpd.conf file in your Apache 1.x server installation:
LoadModule weblogic_module libexec/mod_wl.so AddModule mod_weblogic.c
- For Apache 2.x, install the plug-in by copying the mod_wl_20.so file to the APACHE_HOME/modules directory and adding the following line to your APACHE_HOME/conf/httpd.conf file manually:
LoadModule weblogic_module modules/mod_wl_20.so
- For Apache 1.x, use a command shell to navigate to the directory in your WebLogic Server installation that contains the shared object for your platform and activate the weblogic_module by issuing this command (note that have Perl installed to run this Perl script):
- Verify the syntax of the httpd.conf:
APACHE_HOME/bin/apachect1 configtest
APACHE_HOME/bin/Apache -tThe output of this command reports any errors in your httpd.conf file or returns:
Syntax OK
- Edit...
APACHE_HOME/conf/httpd.conf
- Add something like the following lines to httpd.conf
<IfModule worker.c> StartServers 1 MaxClients 75 MinSpareThreads 25 MaxSpareThreads 75 ThreadsPerChild 25 MaxRequestsPerChild 0 ServerLimit 3 </IfModule>
- Add an IfModule block that defines one of the following:
For a non-clustered WebLogic Server use the WebLogicHost and WebLogicPort parameters.
For a cluster of WebLogic Servers use the WebLogicCluster parameter.
For example:
<IfModule mod_weblogic.c> WebLogicHost myweblogic.server.com WebLogicPort 7001 </IfModule>
- To proxy requests by MIME type, add a MatchExpression line to the IfModule block. Note that if both MIME type and proxying by path are enabled, proxying by path takes precedence over proxying by MIME type.
For example, the following IfModule block for a non-clustered WebLogic Server specifies that all files with MIME type .jsp are proxied:
<IfModule mod_weblogic.c> WebLogicHost myweblogic.server.com WebLogicPort 7001 MatchExpression *.jsp </IfModule>
You can also use multiple MatchExpressions, for example:
<IfModule mod_weblogic.c> WebLogicHost myweblogic.server.com WebLogicPort 7001 MatchExpression *.jsp MatchExpression *.xyz </IfModule>
If you are proxying requests by MIME type to a cluster of WebLogic Servers, use the WebLogicCluster parameter instead of the WebLogicHost and WebLogicPort parameters. For example:
<IfModule mod_weblogic.c> WebLogicCluster w1s1.com:7001,w1s2.com:7001,w1s3.com:7001 MatchExpression *.jsp MatchExpression *.xyz </IfModule>
- To proxy requests by path, use the Location block and the SetHandler statement. For example the following Location block proxies all requests containing /weblogic in the URL:
<Location /weblogic> SetHandler weblogic-handler WebLogicHost myweblogic.server.com WebLogicPort 7001 Debug ALL WLLogFile /tmp/wlproxy.log PathTrim /weblogic </Location>
The PathTrim parameter specifies a string trimmed from the beginning of the URL before the request is passed to the WebLogic Server instance.
- Optionally, enable HTTP tunneling for t3 or IIOP.
- To enable HTTP tunneling if you are using the t3 protocol and weblogic.jar, add the following Location block to the httpd.conf file:
<Location /HTTPClnt> SetHandler weblogic-handler </Location>
- To enable HTTP tunneling if you are using the IIOP, the only protocol used by the WebLogic Server thin client, wlclient.jar, add the following Location block to the httpd.conf file:
<Location /iiop> SetHandler weblogic-handler </Location>
- To enable HTTP tunneling if you are using the t3 protocol and weblogic.jar, add the following Location block to the httpd.conf file:
- Define any additional parameters for the Apache HTTP Server Plug-In.
The Apache HTTP Server Plug-In recognizes the parameters listed in General Parameters for Web Server Plug-Ins. To modify the behavior of your Apache HTTP Server Plug-In, define these parameters either:
- Start (or restart if you have changed the configuration) Apache HTTP Server.
- Test the plug-in by opening a browser and setting the URL to the Apache Server + "/weblogic/", which should bring up the default WebLogic Server HTML page, welcome file, or default servlet, as defined for the default Web Application on WebLogic Server. For example:
http://myApacheserver.com/weblogic/
Use SSL with the Apache Plug-In
You can use SSL to protect the connection between the Apache HTTP Server Plug-In and WebLogic Server.
The Apache HTTP Server Plug-In does not use the transport protocol (http or https) specified in the HTTP request (usually by the browser) to determine whether or not the SSL protocol is used to protect the connection between the Apache HTTP Server Plug-In and WebLogic Server.
Although two-way SSL can be used between the HTTP client and Apache HTTP server, note that one-way SSL is used between Apache HTTP Server and WebLogic Server.
Configure SSL Between the Apache HTTP Server Plug-In and WebLogic Server
To use the SSL protocol between Apache HTTP Server Plug-In and WebLogic Server:
- Configure WebLogic Server for SSL.
- Configure the WebLogic Server SSL listen port.
- In the Apache Server, set the WebLogicPort parameter in the httpd.conf file to the WebLogic Server SSL listen port configured in step 2.
- In the Apache Server, set the SecureProxy parameter in the httpd.conf file to ON.
- Set any additional parameters in the httpd.conf file that define information about the SSL connection.
- Web server plug-ins require a trusted Certificate Authority file in order to use SSL between the plug-in and WebLogic Server. Use Sun Microsystem's keytool utility to export a trusted Certificate Authority file from the DemoTrust.jks keystore file that resides in BEA_HOME/wlserver81/server/lib.
- To extract the wlsdemoca file, for example, use the command:
keytool -export -file trustedcafile.der -keystore DemoTrust.jks -alias wlsdemoca
Change the alias name to obtain a different trusted CA file from the keystore.
To look at all of the keystore's trusted CA files, use:
keytool -list -keystore DemoTrust.jks
Press enter if prompted for password.
- To convert the Certificate Authority file to pem format:
java utils.der2pem trustedcafile.der
- To extract the wlsdemoca file, for example, use the command:
Issues with SSL-Apache Configuration
Three known issues arise when you configure the Apache plug-in to use SSL:
- The PathTrim parameter (see General Parameters for Web Server Plug-Ins) must be configured inside the <Location> tag.
The following configuration is incorrect:
<Location /weblogic> SetHandler weblogic-handler </Location> <IfModule mod_weblogic.c> WebLogicHost localhost WebLogicPort 7001 PathTrim /weblogic </IfModule>
The following configuration is the correct setup:
<Location /weblogic> SetHandler weblogic-handler PathTrim /weblogic </Location>
- The Include directive does not work with Apache SSL. You must configure all parameters directly in the httpd.conf file. Do not use the following configuration when using SSL:
<IfModule mod_weblogic.c> MatchExpression *.jsp Include weblogic.conf </IfModule>
- The current implementation of the WebLogic Server Apache Plug-In does not support the use of multiple certificate files with Apache SSL.
Connection Errors and Clustering Failover
When the Apache HTTP Server Plug-In attempts to connect to WebLogic Server, the plug-in uses several configuration parameters to determine how long to wait for connections to the WebLogic Server host and, after a connection is established, how long the plug-in waits for a response. If the plug-in cannot connect or does not receive a response, the plug-in attempts to connect and send the request to other WebLogic Server instances in the cluster. If the connection fails or there is no response from any WebLogic Server in the cluster, an error message is sent.
Figure 2-1 demonstrates how the plug-in handles failover.
Possible Causes of Connection Failures
Failure of the WebLogic Server host to respond to a connection request could indicate the following problems:
- Pysical problems with the host machine
- Network problems
- Other server failures
Failure of all WebLogic Server instances to respond could indicate the following problems:
- WebLogic Server is not running or is unavailable
- A hung server
- A database problem
- An application-specific failure
Tuning to Reduce Connection_Refused Errors
Under load, an Apache plug-in may receive CONNECTION_REFUSED errors from a back-end WebLogic Server instance. Follow these tuning tips to reduce CONNECTION_REFUSED errors:
- Increase the AcceptBackLog setting in the configuration of your WebLogic Server domain. See Tuning Connection Backlog Buffering
- On Apache 2.x, set the KeepAlive directive in the httpd.conf file to On. For example:
# KeepAlive: Whether or not to allow persistent connections (more than # one request per connection). Set to "Off" to deactivate. # KeepAlive On
See Apache HTTP Server 2.0 documentation at http://httpd.apache.org/docs-project/.
Apache 1.3.x does not support this feature.
- Decrease the time wait interval. This setting varies according to the operating system you are using. For example:
- On Windows NT, set the TcpTimedWaitDelay on the proxy and WebLogic Server servers to a lower value. Set the TIME_WAIT interval in Windows NT by editing the registry key under HKEY_LOCAL_MACHINE:
SYSTEM/CurrentControlSet/Services/Tcpip/Parameters/TcpTimedWaitDelay
If this key does not exist you can create it as a DWORD value. The numeric value is the number of seconds to wait and may be set to any value between 30 and 240. If not set, Windows NT defaults to 240 seconds for TIME_WAIT.
- On Windows 2000, lower the value of the TcpTimedWaitDelay by editing the registry key under HKEY_LOCAL_MACHINE:
SYSTEM/CurrentControlSet/Services/Tcpip/Parameters
- On Solaris, reduce the setting tcp_time_wait_interval to one second (for both the WebLogic Server machine and the Apache machine, if possible):
$ndd /dev/tcp param name to set - tcp_time_wait_interval value=1000
- On Windows NT, set the TcpTimedWaitDelay on the proxy and WebLogic Server servers to a lower value. Set the TIME_WAIT interval in Windows NT by editing the registry key under HKEY_LOCAL_MACHINE:
- Increase the open file descriptor limit on your your machine. This limit varies by operating system. Using the limit (.csh) or ulimit (.sh) directives, you can make a script to increase the limit. For example:
#!/bin/sh ulimit -S -n 100 exec httpd
- On Solaris, increase the values of the following tunables on the WebLogic Server machine:
- tcp_conn_req_max_q
- tcp_conn_req_max_q0
Failover with a Single, Non-Clustered WebLogic Server
If you are running only a single WebLogic Server instance the plug-in only attempts to connect to the server defined with the WebLogicHost parameter. If the attempt fails, an HTTP 503 error message is returned. The plug-in continues trying to connect to that same WebLogic Server instance until ConnectTimeoutSecs is exceeded.
The Dynamic Server List
When you use the WebLogicCluster parameter in your httpd.conf or weblogic.conf file to specify a list of WebLogic Servers, the plug-in uses that list as a starting point for load balancing among the members of the cluster. After the first request is routed to one of these servers, a dynamic server list is returned containing an updated list of servers in the cluster. The updated list adds any new servers in the cluster and deletes any that are no longer part of the cluster or that have failed to respond to requests. This list is updated automatically with the HTTP response when a change in the cluster occurs.
Failover, Cookies, and HTTP Sessions
When a request contains session information stored in a cookie or in the POST data, or encoded in a URL, the session ID contains a reference to the specific server instance in which the session was originally established (called the primary server) and a reference to an additional server where the original session is replicated (called the secondary server). A request containing a cookie attempts to connect to the primary server. If that attempt fails, the request is routed to the secondary server. If both the primary and secondary servers fail, the session is lost and the plug-in attempts to make a fresh connection to another server in the dynamic cluster list. See Figure 2-1 Connection Failover.
Note: If the POST data is larger than 64K, the plug-in will not parse the POST data to obtain the session ID. Therefore, if you store the session ID in the POST data, the plug-in cannot route the request to the correct primary or secondary server, resulting in possible loss of session data.
Figure 2-1 Connection Failover
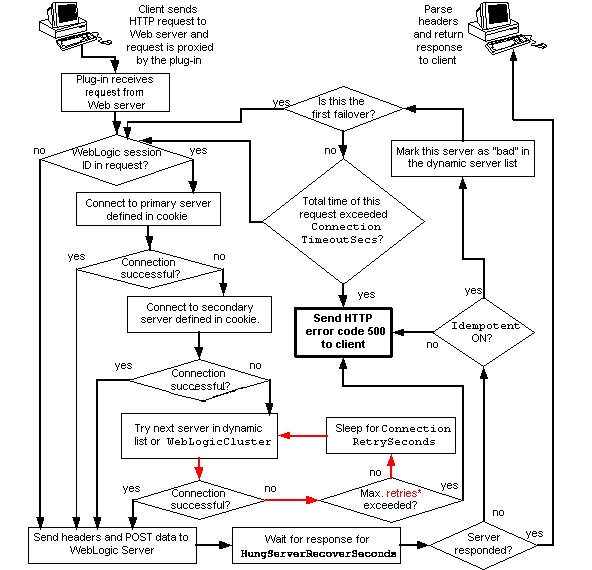 The Maximum number of retries allowed in the red loop is equal to
The Maximum number of retries allowed in the red loop is equal to
ConnectTimeoutSecs ÷ ConnectRetrySecs.
Including a weblogic.conf File in the httpd.conf File
If you want to keep several separate configuration files, you can define parameters in a separate configuration file called weblogic.conf file, by using the Apache Include directive in an IfModule block in the httpd.conf file:
<IfModule mod_weblogic.c>
# Config file for WebLogic Server that defines the parameters
Include conf/weblogic.conf
</IfModule>
The syntax of weblogic.conf files is the same as that for the httpd.conf file.
This section describes how to create weblogic.conf files, and includes sample weblogic.conf files.
Creating weblogic.conf Files
Be aware of the following when constructing a weblogic.conf file.
- If you are using SSL between the Apache HTTP Server Plug-In and WebLogic Server, you cannot define parameters in a file accessed, as the weblogic.conf file is, via the Apache Include directive.
- Enter each parameter on a new line. Do not put `=' between a parameter and its value. For example:
PARAM_1 value1 PARAM_2 value2 PARAM_3 value3
- If a request matches both a MIME type specified in a MatchExpression in an IfModule block and a path specified in a Location block, the behavior specified by the Location block takes precedence.
- If you define the CookieName parameter , define it in an IfModule block.
- If you use an Apache HTTP Server <VirtualHost> block, include all configuration parameters (MatchExpression, for example) for the virtual host within the <VirtualHost> block (see Apache Virtual Host documentation).
- BEA recommends that you use the MatchExpression statement instead of the <files> block.
Sample weblogic.conf Configuration Files
The following examples of weblogic.conf files may be used as templates that you can modify to suit your environment and server. Lines beginning with # are comments.
Example Using WebLogic Clusters
# These parameters are common for all URLs which are
# directed to the current module. If you want to override
# these parameters for each URL, you can set them again in
# the <Location> or <Files> blocks. (Except WebLogicHost,
# WebLogicPort, WebLogicCluster, and CookieName.)
<IfModule mod_weblogic.c>
WebLogicCluster w1s1.com:7001,w1s2.com:7001,w1s3.com:7001
ErrorPage http://myerrorpage.mydomain.com
MatchExpression *.jsp
</IfModule>
Example Using Multiple WebLogic Clusters
In this example, the MatchExpression parameter syntax for expressing the filename pattern, the WebLogic Server host to which HTTP requests should be forwarded, and various other parameters is as follows:
MatchExpression [filename pattern] [WebLogicHost=host] | [paramName=value]
The first MatchExpression parameter below specifies the filename pattern *.jsp, and then names the single WebLogicHost. The paramName=value combinations following the pipe symbol specify the port at which WebLogic Server is listening for connection requests, and also activate the Debug option. The second MatchExpression specifies the filename pattern *.http and identifies the WebLogicCluster hosts and their ports. The paramName=value combination following the pipe symbol specifies the error page for the cluster.
# These parameters are common for all URLs which are # directed to the current module. If you want to override # these parameters for each URL, you can set them again in # the <Location> or <Files> blocks (Except WebLogicHost, # WebLogicPort, WebLogicCluster, and CookieName.) <IfModule mod_weblogic.c> MatchExpression *.jsp WebLogicHost=myHost|WebLogicPort=7001|Debug=ON MatchExpression *.html WebLogicCluster=myHost1:7282,myHost2:7283|ErrorPage=http://www.xyz.com/error.html </IfModule>
Example Without WebLogic Clusters
# These parameters are common for all URLs which are
# directed to the current module. If you want to override
# these parameters for each URL, you can set them again in
# the <Location> or <Files> blocks (Except WebLogicHost,
# WebLogicPort, WebLogicCluster, and CookieName.)
<IfModule mod_weblogic.c>
WebLogicHost myweblogic.server.com
WebLogicPort 7001
MatchExpression *.jsp
</IfModule>
Template for the Apache HTTP Server httpd.conf File
This section contains a sample httpd.conf file for Apache 1.3. You can use this sample as a template and modify it to suit your environment and server. Lines beginning with # are comments.
Note that Apache HTTP Server is not case sensitive.
####################################################
APACHE-HOME/conf/httpd.conf file
####################################################
LoadModule weblogic_module libexec/mod_wl.so
AddModule mod_weblogic.c
<Location /weblogic>
SetHandler weblogic-handler
PathTrim /weblogic
ErrorPage http://myerrorpage1.mydomain.com
</Location>
<Location /servletimages>
SetHandler weblogic-handler
PathTrim /something
ErrorPage http://myerrorpage1.mydomain.com
</Location>
<IfModule mod_weblogic.c>
MatchExpression *.jsp
WebLogicCluster w1s1.com:7001,w1s2.com:7001,w1s3.com:7001
ErrorPage http://myerrorpage.mydomain.com
</IfModule>
Setting Up Perimeter Authentication
Use perimeter authentication to secure WebLogic Server applications that are accessed via the Apache Plug-In.
A WebLogic Identity Assertion Provider authenticates tokens from outside systems that access your WebLogic Server application, including users who access your WebLogic Server application through the Apache HTTP Server Plug-In. Create an Identity Assertion Provider that will safely secure your Plug-In as follows:
- Create a custom Identity Assertion Provider on your WebLogic Server application. See How to Develop a Custom Identity Assertion Provider in Developing Security Providers for WebLogic Server.
- Configure the custom Identity Assertion Provider to support the Cert token type and make Cert the active token type. See How to Create New Token Types in Developing Security Providers for WebLogic Server.
- Set clientCertProxy to True in the web.xml deployment descriptor file for the Web application (or, if using a cluster, optionally set the Client Cert Proxy Enabled attribute to true for the whole cluster on the Administration Console Cluster-->Configuration-->General tab).
- Once you have set clientCertProxy, be sure to use a connection filter to ensure that WebLogic Server accepts connections only from the machine on which the Apache Plug-In is running. See Using Network Connection Filters in Programming WebLogic Security.
See Identity Assertion Providers in Developing Security Providers for WebLogic Server.
|
|
|
Limitations in Apache Version 1.3.x
Version 1.3x of the Apache HTTP Server has several limitations with the WebLogic Server plug-in that do not exist in later versions.
Keep-Alive Connections Not Supported
Version 1.3.x of the Apache HTTP Server Plug-In creates a socket for each request and closes the socket after reading the response. Because Apache HTTP Server is multiprocessed, connection pooling and keep-alive connections between WebLogic Server and the Apache HTTP Server Plug-In cannot be supported.
Inconsistent States
The Apache HTTP Server has a multi-process architecture, and the state of the plug-in cannot be synchronized across multiple child processes. The following types of problems may occur:
- In a clustered environment, a plug-in may dispatch requests to an unavailable WebLogic Server instance because the DynamicServerList is not current in all plug-in processes.
- In non-clustered environment, a plug-in may lose the stickiness of a session created after restarting WebLogic Server instances, because some plug-in processes do not have the new JVMID of those restarted servers, and treat them as unknown JVMIDs.
To temporarily correct inconsistencies of this type, restart or send a HUP signal kill(-HUP) to the Apache server to refresh all plug-in processes.
To avoid these issues, configure Apache 2.0 with the mpm_worker_module.
Keep-Alive Connections Supported in Apache Version 2.0
Version 2.0 of the Apache HTTP Server Plug-In improves performance by using a reusable pool of connections from the plug-in to WebLogic Server. The plug-in implements HTTP 1.1 keep-alive connections between the plug-in and WebLogic Server by reusing the same connection in the pool for subsequent requests from the same client. If the connection is inactive for more than 30 seconds, (or a user-defined amount of time) the connection is closed and returned to the pool. You can disable this feature if desired.
Proxying Requests
The plug-in proxies requests to WebLogic Server based on a configuration that you specify. You can proxy requests based on the URL of the request (or a portion of the URL). This is called proxying by path. You can also proxy requests based on the MIME type of the requested file. Or you can use a combination of the two methods. If a request matches both criteria, the request is proxied by path. You can also specify additional parameters for each type of request that define additional behavior of the plug-in.
Certifications
The Apache HTTP Server Plug-In is supported on Linux, AIX, Solaris, Windows, and HPUX11 platforms. For information on support for specific versions of Apache, see the BEA WebLogic Server Certifications Page
Install the Apache HTTP Server Plug-In as a Statically Linked Module
To install the Apache HTTP Server Plug-In as a statically linked module:
- Unpack the Apache Plug-In distribution using the following command:
tar -xvf apache_1.3.x.tar
- Within the unpacked distribution switch to the src/modules directory.
- Create a directory called weblogic.
- Locate the linked library file for your platform.
Each library file is distributed as a separate version, depending on the platform and the encryption strength for SSL (regular or 128-bit - 128-bit versions are only installed if you install the 128-bit version of WebLogic Server). The library files are located in the following directories of your WebLogic Server installation:
Operating System
Shared Object Location
Solaris WL_HOME/Server/lib/solaris Linux WL_HOME/Server/lib/linux HPUX11 WL_HOME/Server/lib/hpux11 Warning: If you are running Apache 2.0.x server on HP-UX11, set the environment variables specified below before you build the Apache server. Because of a problem with the order in which linked libraries are loaded on HP-UX, a core dump can result if the load order is not preset as an environment variable before building. Set the following environment variables before proceeding with the Apache configure, make, and make install steps, (described in Apache HTTP Server documentationat http://httpd.apache.org/docs-2.1/install.html#configure):
export EXTRA_LDFLAGS="-lstd -lstream -lCsup -lm -lcl -ldld -lpthread"
Choose the appropriate shared object from the following table.
Apache Version
Regular Strength Encryption
128-bit
EncryptionStandard Apache Version 1.3.x libweblogic.a libweblogic128.a If you are using the Gnu C Compiler (gcc), gcc 2.95.x is the recommended version.
- Copy Makefile.libdir, Makefile.tmpl from the lib directory of your WebLogic Server installation to...
src/modules/weblogic
- Copy libweblogic.a (use libweblogic128.a instead, if you are using 128 bit security.) from the same directory containing the linked library file to src/modules/weblogic.
- If you are using regular strength encryption, execute the following command from the Apache 1.3 home directory:
configure --activate-module=src/modules/weblogic/libweblogic.a
- If you are using 128 bit encryption, execute the following command (on a single line) from the Apache 1.3 home directory:
configure--activate-module=src/modules/weblogic/libweblogic128.a
- Execute the following command:
make
- Execute the following command:
make install
- Define any additional parameters for the Apache HTTP Server Plug-In.
The Apache HTTP Server Plug-In recognizes the parameters listed in General Parameters for Web Server Plug-Ins. To modify the behavior of your Apache HTTP Server Plug-In, define these parameters:
- Verify the syntax of APACHE_HOME/conf/httpd.conf:
For Apache 1.x,
APACHE_HOME/bin/apachect1 configtest
For Apache 2.x,
APACHE_HOME/bin/Apache -t
The output of this command reports any errors in your httpd.conf file or returns:
Syntax OK
- Restart Weblogic Server.
- Start (or restart if you have changed the configuration) Apache HTTP Server.
- Test the plug-in by opening a browser and setting the URL to the Apache Server + "/weblogic/", which should bring up the default WebLogic Server HTML page, welcome file, or default servlet, as defined for the default Web Application on WebLogic Server. For example:
http://myApacheserver.com/weblogic/