Single sign-on for HTTP requests using SPNEGO Web authentication
We can authenticate HTTP requests for secured resources in WAS using SPNEGO.
New feature: SPNEGO trust association interceptors were introduced in WAS v6.1. In WAS 7.0, this function is now deprecated. SPNEGO Web authentication has taken its place to provide the following enhancements...
- Filters
- Dynamic reload of SPNEGO is provided without the need to stop and restart WAS.
- Fallback to an application login method if SPNEGO Web authentication fails.
- Customization at the WebSphere security domain level.
We can enable either SPNEGO TAI or SPNEGO Web Authentication but not both.
What is SPNEGO?
When WAS global and application security are enabled, and SPNEGO Web authentication is enabled, SPNEGO is initialized when processing a first inbound HTTP request. The Web authenticator component then interacts with SPNEGO, which is defined in the security configuration repository.
When the filter criteria is met, SPNEGO is responsible for authenticating access to the secured resource that is identified in the HTTP request.
Some external components are required to enable the operation of SPNEGO, including...
- Microsoft Windows 2000 or Windows 2003 Servers with Active Directory domain and associated Kerberos Key Distribution Center (KDC).
- A client application that supports the SPNEGO Web authentication mechanism, as defined in IETF RFC 2478. For example...
- Microsoft .NET
- Web service
- J2EE client
- Microsoft Internet Explorer
- Mozilla Firefox V1.0
The authentication of HTTP requests is triggered by the requestor (the client-side), which generates a SPNEGO token. WAS receives this token. Specifically, the SPNEGO Web authentication decodes and retrieves the requester's identity from the SPNEGO token. The identity is used to establish a secure context between the requester and the appserver.
SPNEGO Web authentication is a server-side solution in WAS. Client-side applications are responsible for generating the SPNEGO token for use by SPNEGO Web authentication. The requester's identity in the WAS security registry must be identical to the identity that the SPNEGO Web authentication retrieves. An identical match does occur when MS Windows AD server is the LDAP server used in WAS. A custom login module is available as a plug-in to support custom mapping of the identity from the AD to the WAS security registry.
WAS validates the identity against its security registry. If the validation is successful, the client Kerberos ticket and GSS delegation credential are retrieved and placed in the client subject, which then produces a LTPA security token. It then places and returns a cookie to the requester in the HTTP response. Subsequent HTTP requests from this same requester to access additional secured resources in WAS use the LTPA security token previously created to avoid repeated login challenges.
The Web administrator has access to the following SPNEGO security components and associated configuration data...
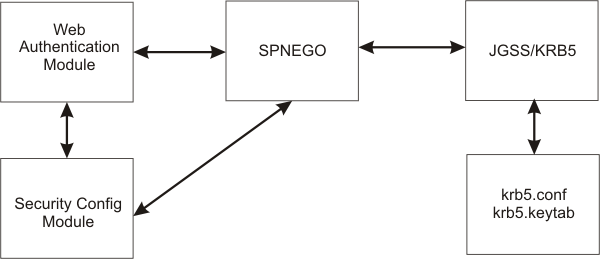
The benefits of SPNEGO Web authentication
The benefits of having WAS use SPNEGO as the Web authentication service for WAS include the following:
- An integrated single sign-on environment with MS Windows 2000 or 2003 Servers using AD domain is established.
- The cost of administering a large number of ids and passwords is reduced.
- A secure and mutually authenticated transmission of security credentials from the Web browser or MS .NET clients is established.
- Interoperability with Web services and MS .NET, or Web service applications that use SPNEGO authentication at the transport level is achieved.
- With Kerberos authentication support, SPNEGO Web authentication can provide an end-to-end SPNEGO to Kerberos solution and preserve the Kerberos credential from the client.
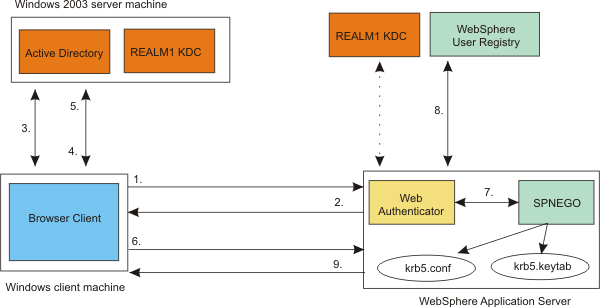
SPNEGO Web authentication in a single Kerberos realm
SPNEGO Web authentication is supported in a single Kerberos realm.
The challenge-response handshake process...
In the figure above, the following events occur:
Other clients (for example, Web Services, .NET and J2EE) that support SPNEGO do not have to follow the challenge-response handshake process as shown above. Those clients can obtain a ticket-granting ticket (TGT) and a Kerberos service ticket for the target server, create a SPNEGO token, insert it in the HTTP header, and then follow the normal process for creating an HTTP request.
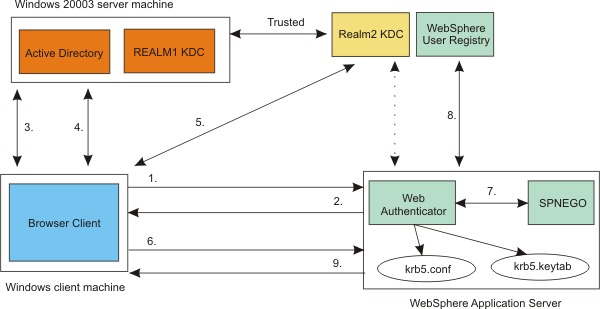
SPNEGO Web authentication is also supported in a trusted Kerberos realm.
The challenge-response handshake process...
In the figure above, the following events occur:
In the trusted Kerberos realms environment, be aware of the following:
Before you set up SPNEGO Web authentication in the admin console or by using wsadmin commands, perform the following steps to set up Kerberos as the authentication mechanism for WAS.
Kerberos authentication mechanism on the server side must be done by the system administrator. The Kerberos keytab file must be protected.
The format of the SPN is...
HTTP/<fully qualified hostname>
SPNEGO uses this SPN to validate and establish the security context with the SPNEGO requester.
To use a remote HTTP server, create the SPN for the remote proxy server and add the proxy SPN and key to the keytab file.
The Kerberos keytab file (krb5.keytab) contains all of the SPNs for the node and must be protected.
This file can be placed in the config/cells/<cell_name> directory.
SPNEGO Web authentication and Kerberos authentication both use the same Kerberos configuration and keytab files.
SPNEGO Web authentication in a trusted Kerberos realm
Set up SPNEGO as the Web authentication mechanism for
For information about how to set up SPNEGO Web authentication for WAS by using wsadmin commands, read about SPNEGO Web authentication configuration commands.
The client, WebSphere application server and KDC machines must keep the clock synchronized. The best practice is to use a time server to keep all of the systems synchronized.
Related tasks
Enable and configuring SPNEGO Web authentication
Set the client browser to use SPNEGO
Create a Kerberos service principal and keytab file
Create a single sign-on for HTTP requests using SPNEGO Web authentication
Related
SPNEGO Web authentication configuration commands
SPNEGO Web authentication filter commands
SPNEGO troubleshooting tips