The failover environment
The failover cookie is not actually a mechanism for maintaining sessions; it is a mechanism for transparently reauthenticating the user. Failover authentication is most commonly used in a scenario where client requests are directed by a load balancing mechanism to two or more replicated WebSEAL servers.
The replicated servers have identical configuration. They contain replica copies of the WebSEAL protected object space, junction database, and (optionally) dynurl database.
The client is not aware of
the replicated front-end server configuration.
The load balancing mechanism is the single point of contact for the requested resource. The load balancer connects the client with an
available server.
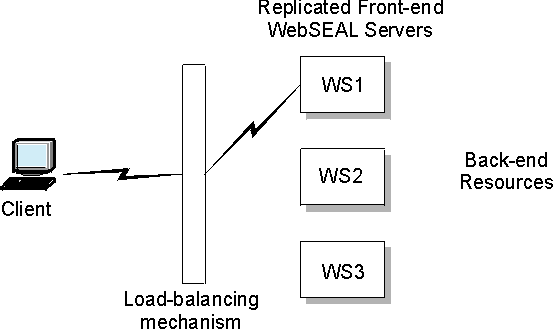
If the server where the client is connected suddenly becomes unavailable, the load balancer redirects the request to one of the other replicated servers. This action causes the loss of the original session-to-credential mapping. The client is new to this substitute server and is normally forced to login again.
The purpose of failover authentication is to prevent forced login when the WebSEAL server that has the original session with the client suddenly becomes unavailable. Failover authentication enables the client to connect to another WebSEAL server, and create an authentication session containing the same user session data and user credentials.
Failover authentication in a replicated server deployment provides two useful features:
- Performance improvements through load balancing
- Failover of client sessions between WebSEAL servers
References:
- For more information on the replication of WebSEAL servers, see Replicating front-end WebSEAL servers.
- For information on failover solutions in an environment without session affinity (non-sticky), see Failover for non-sticky failover environments.
Parent topic: Failover authentication concepts