Network Deployment (Distributed operating systems), v8.0 > Secure applications and their environment > Authenticate users > Implement single sign-on to minimize web user authentications > Create a single sign-on for HTTP requests using SPNEGO Web authentication > 4. Configure the client application on the client application machine
Web browsers and SPNEGO
Configure Internet Explorer
- At the desktop, log on to the windows active directory domain.
- Activate Internet Explorer.
- In the Internet Explorer window, click...
- Tools | Internet Options | Security | Local intranet icon | Sites
- In the Local intranet window, verify the check box to "Include all local (intranet) not listed in other zones" is selected.

Click Advanced.
- In the Local intranet window, fill in the field...
- Add this web site to the zone
...with the web address of the host name so that the single sign-on (SSO) can be enabled for the list of websites shown in the websites field. Your site information technology staff provides this information. Click OK to complete this step and close the Local intranet window.
- Add this web site to the zone
- On the Internet Options window, click the Advanced tab and scroll to Security settings. Ensure that the Enable Integrated Windows Authentication (requires restart) box is selected.
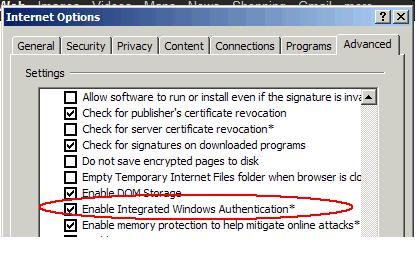
- Click OK. Restart your Microsoft Internet Explorer to activate this configuration.
Configure Firefix browser
- At the desktop, log in to the windows active directory domain.
- Activate Firefox.
- At the address field, type about:config.
- In the Filter, type network.n
- Double click on network.negotiate-auth.trusted-uris.
This preference lists the sites that are permitted to engage in SPNEGO Authentication with the browser. Enter a comma-delimited list of trusted domains or URLs.
We must set the value for network.negotiate-auth.trusted-uris.
- If the deployed SPNEGO solution is using the advanced Kerberos feature of Credential Delegation double click on network.negotiate-auth.delegation-uris.
This preference lists the sites for which the browser may delegate user authorization to the server. Enter a comma-delimited list of trusted domains or URLs.
- Click OK. The configuration appears as updated.
- Restart your Firefox browser to activate this configuration.
Results
Your Internet browser is properly configured for SPNEGO authentication. We can use applications that are deployed in WAS that use secured resources without being repeatedly requested for a user ID and password.
If you are prompted multiple times for a user ID and password, make sure that you enabled SPNEGO support on your client browser per the instructions above. We must also make sure that the Allow fall back to application authentication mechanism support option is enabled on the WAS server side.
Create a single sign-on for HTTP requests using SPNEGO Web authentication
Create a Kerberos service principal (SPN) and keytab file on your Microsoft domain controller machine
Create SPNEGO tokens for J2EE, .NET, Java, web service clients for HTTP requests
Create a Kerberos service principal name and keytab file
Set SPNEGO web authentication filters
Related
SPNEGO web authentication configuration commands
SPNEGO web authentication filter commands
SPNEGO web authentication enablement
SPNEGO web authentication filter values