Set up Active Directory
Content
Active Directory and SSL
If you set up WebSphere Portal with Active Directory without SSL enabled, we cannot set passwords in sign up or user creation correctly. You would need to manually reset passwords on Active Directory. However, IBM recommends that you first get LDAP (non-SSL) successfully working before setting up LDAP over SSL. This allows us to verify that the directory is responding to LDAP requests before setting it up for SSL.
The following is an outline of requirements for setting up SSL on a Windows 2000 Domain Controller using the Microsoft Enterprise Certificate Authority:
- Install an Enterprise Certificate Authority on a Windows 2000 Domain Controller, which installs a certificate on a server or install a third-party certificate on the Domain Controller.
- Click...
Start | All Programs | Administrative Tools | Active Directory | Users and Computer
- In the Active Directory Users and Computers window, right-click on the domain name and select Properties.
- In the Domain Properties dialog box, select the Group Policy tab.
- Select the Default Domain Policy group policy and then click Edit.
- Select Windows Settings under Computer Configuration.
- Select Security Settings and then select Public Key Policies.
- Select Automatic Certificate Request Settings.
- Use the wizard to add a policy for Domain Controllers.
When these requirements are complete, all domain controllers request a certificate and support LDAP over SSL using port 636.
Example of the Active Directory structure
The following schema is an example for Active Directory and is referenced throughout the documentation for consistency. The example below is designed to help you determine the appropriate values when configuring WebSphere Portal to work with the specific directory layout. The values shown match the default values for this LDAP. If you have an existing schema that varies from this example, replace the example values with the values. For instance, cn is shown as the group prefix; replace cn with the group prefix for the schema.
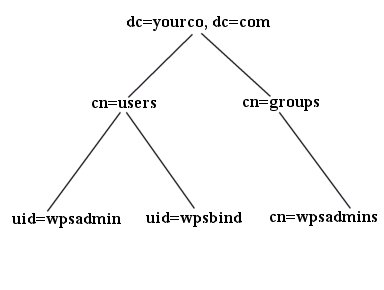
LDAP suffix dc=yourco,dc=com user prefix uid user suffix cn=users group prefix cn group suffix cn=groups Portal admin DN uid=wpsadmin,cn=users,dc=yourco,dc=com Portal admin group cn=wpsadmins,cn=groups,dc=yourco,dc=com
Parent Topic
Steps to configure an Active Directory LDAP