Configure form-based authentication
One of the login challenges defined in J2EE Specification is the form-based login. It enables the application developer to customize the login process and present an application-specific form by making use of the Form Login Authentication mechanism.
Form login works in the following manner:
- An unauthenticated user requests a resource protected by the Form Login authentication type.
- The application server redirects the request to the Login Form defined previously in the Web deployment descriptor.
- On the HTML login form, the user enters the user ID and password and submits the form.
- The action, triggered by the form submission, refers to a special servlet j_security_check. The Web container, after receiving a request for the j_security_check servlet, dispatches the information to the application server's security mechanism to perform the authentication.
- If the servlet authenticates the user successfully, the originally requested resource is displayed.
If you select LTPA as the authentication mechanism under Global Security settings and use form login in any Web application, also enable Single Sign-On (SSO). If SSO is not enabled, authentication during form login fails with a configuration error. SSO is required because it generates an HTTP cookie that contains information representing the identity of the user to the Web browser. This information is needed to authorize protected resources when a form login is used.
Form login configuration
The following steps show how to configure form-based login using the Rational Application Developer.
- Load your Web application module into the Rational Application Developer, in our example: itsobank.ear.
- Within J2EE perspective, click Dynamic Web Projects | itsobank to expand the tree.
- Double-click the Deployment Descriptor of itsobankWeb Module. The Web Deployment descriptor page will open.
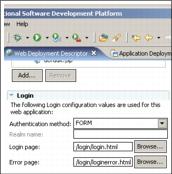
- Select the Pages tab and scroll down.
- In the Login section, select the FORM authentication method.
- For the Login Page, specify...
/login/login.html...and for the Error Page specify...
/login/loginerror.html- Save the changes.
Setting the Authentication Method for the application Web module creates a <login-config> section in a Web deployment descriptor XML file, as shown in the following example.
<login-config> <auth-method>FORM</auth-method> <realm-name>ITSO Bank</realm-name> <form-login-config> <form-login-page>/login/login.html</form-login-page> <form-error-page>/login/loginerror.html</form-error-page> </form-login-config> </login-config>Simple form-based login does not require any extra code development on the server side. Servlet j_security_check used by WebSphere Application Server enforces only the name of the input fields that the developer should put in the custom Login Form.
These fields are as follows:
- j_username should be the input field in which a user will type the user name.
- j_password should be the input field into which user will type the password.
The action required for the HTTP POST method is j_security_check. A simple HTML code for the custom Login Form is given below...
<!-- ............... --> <form method="post" action="/itsobank/j_security_check"> User name:<input type="text" name="j_username"> Password:<input type="password" name="j_password"> <input type="submit" name="action" value="Login"> </form> <!-- ............... -->
Note: The j_security_check servlet will not work when Global Security is disabled; the application server will return a Page Not Found error.
This is also true for the ibm_security_logout servlet.