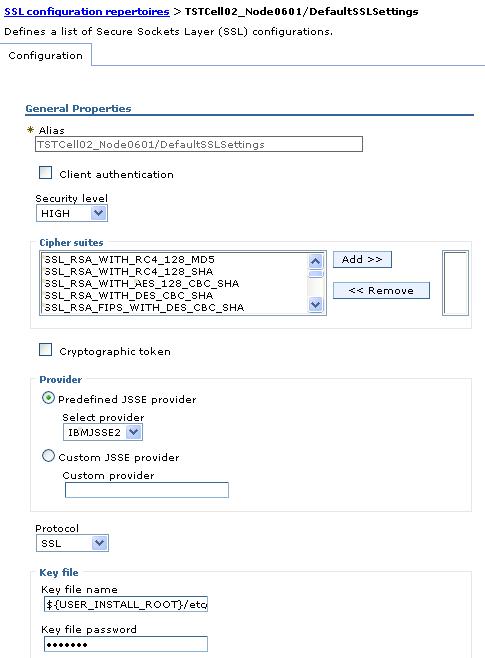
Repertoire settings
Use this page to configure SSL or JSSE settings. To configure SSL, define an SSL configuration repertoire, which contains the details necessary for building an SSL connection, such as the location of the key files, their type and the available ciphers. WAS provides a default repertoire called DefaultSSLSettings.
To view this administrative console page, click...
Security | SSL | alias_name
- Provider
-
Refers to a package that implements a subset of the Java security API cryptography aspects. WAS has the following predefined providers.
- IBMJSSE
- IBMJSSE2
- IBMJSSEFIPS
If you select the Use FIPS option on the global security panel, IBMJSSE2 uses the IBMJCEFIPS provider that is FIPS certified.
If you select Custom JSSE provider, enter a custom provider. For a custom provider, you first must enter the cipher suites through Custom properties under Additional Properties. Cipher suites and protocol values depend upon the provider.
The name for the Cipher suite property is...
com.ibm.ssl.enabledCiphersuites
The name for the protocol property is...
com.ibm.ssl.protocol
Note: We can only specify the IBMJSSE2 provider for transports using the channel framework, including HTTP and JMS. Any other provider specified causes the server to fail initialization.
- Protocol
-
Specifies which SSL protocol to use.
If you are using a FIPS-approved custom JSSE provider, select a TLS protocol. However, because the FIPS-approved JSSE providers are not backwards-compatible, a server that uses the TLS protocol cannot communicate with a client that uses an SSL protocol.
Default SSLv3 Range SSL, SSLv2, SSLv3, TLS, TLSv1
Configuration tab
- Alias
-
Name of the specific SSL setting
Data type: String - Key file name
-
Specifies the fully qualified path to the SSL key file that contains public keys and might contain private keys.
We can create an SSL key file with the key management utility, or this file can correspond to a hardware device if one is available. In either case, this option indicates the source for personal certificates and for signer certificates unless a trust file is specified.
The default SSL key files, DummyClientKeyFile.jks and DummyServerKeyFile.jks, contains a self-signed personal test certificate expiring on March 17, 2005. The test certificate is only intended for use in a test environment. The default SSL key files should never be used in a production environment because the private keys are the same on all the WAS installations.
Data type: String - Client authentication
-
Specifies whether to request a certificate from the client for authentication purposes when making a connection.
This attribute is only valid when it is used by the Web container HTTP transport.
When performing client authentication with the Internet InterORB Protocol (IIOP) for EJB requests, click Security > Global security. Under Authentication, click Authentication protocol > CSIv2 inbound authentication or Authentication protocol > CSIv2 outbound authentication. Select the appropriate option under Client certificate authentication.
Default: Disabled Range: Enabled or Disabled - Security level
-
Specifies whether the server selects from a preconfigured set of security levels.
Data type: Valid values include Low, Medium or High. - Low specifies digital signing ciphers only without encryption.
- Medium specifies 40-bit ciphers only including digital signing.
- High specifies 128-bit ciphers only including digital signing.
To specify all ciphers or any particular range, one can set the com.ibm.ssl.enabledCipherSuites property.
See the SSL documentation for more information.
Default: High Range: Low, Medium, or High - Cipher suites
-
Specifies a list of supported cipher suites that can be selected during the SSL handshake. If you select cipher suites individually here, you override the cipher suites set in the Security Level field.
- Key file password
-
Specifies the password for accessing the SSL key file.
Data type: String - Key file format
-
Specifies the format of the SSL key file.
We can choose from the following key file formats: JKS, JCEK, PKCS12. The JKS format does not store a shared key. For more secure key files, use the JCEK format. PKCS12 is the standard file format.
Data type: String Default: JKS Range: JKS, PKCS12, JCEK - Trust file name
-
Specifies the fully qualified path to a trust file containing the public keys.
We can create a trust file with the key management utility included in the WebSphere bin directory. Using the key management utility from Global Security Kit (GSKit) (another SSL implementation) does not work with the Java Secure Socket Extension (JSSE) implementation.
Unlike the SSL key file, no personal certificates are referenced; only signer certificates are retrieved. The default SSL trust files, DummyClientTrustFile.jks and DummyServerTrustFile.jks, contain multiple test public keys as signer certificates that can expire. The following public keys expire on October 13, 2021:
- WebSphere Application Server V4.x test certificates
- WebSphere Application Server V5.x test certificates
- WebSphere Application Server CORBA C++ client
- WebSphere Application Server v6.x test certificates
The test certificates are only intended for use in a test environment.
If a trust file is not specified but the SSL key file is specified, then the SSL key file is used for retrieval of signer certificates as well as personal certificates.
Data type: String - Trust file password
-
Specifies the password for accessing the SSL trust file.
Data type: String - Trust file format
-
Specifies the format of the SSL trust file.
We can choose from the following trust file formats: JKS, JCEK, PKCS12. The JKS format does not store a shared key. For more secure key files, use the JCEK format. PKCS12 is the standard file format.
Data type: String Default: JKS Range: JKS, JCEK, PKCS12
Related Tasks
Configuring FIPS JSSE files