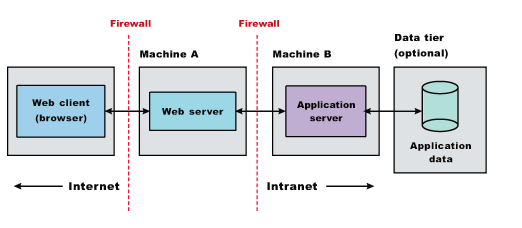
Firewalls and demilitarized zone configurations
Firewalls protect backend resources, such as databases in multiple machine systems. You can also use firewalls to protect Application Servers and Web servers from unauthorized outside access. A demilitarized zone (DMZ) configuration involves multiple firewalls that add layers of security between the Internet and critical data and business logic.
A wide variety of topologies are appropriate for a DMZ environment. Although WAS provides great flexibility in configuring DMZ topologies, the basic locations of elements in a simple DMZ topology follow:
The main purpose of a DMZ configuration is to protect the business logic and data in the environment from unauthorized access. A typical DMZ configuration includes:
- An outer firewall between the public Internet and the Web server or servers processing the requests originating on the company Web site.
- An inner firewall between the Web server and the Application Servers to which it is forwarding requests. Company data also resides behind the inner firewall.
The area between the two firewalls gives the DMZ configuration its name. Additional firewalls can further safeguard access to databases holding administrative and application data.
A DMZ configuration....
- Protects application logic and data.
By creating a buffer between the public Internet Web site and the internal intranet, where Application Servers and the data tier reside. Desirable DMZ topologies do not have databases or appservers with critical business data in the DMZ.
- Supports Network Address Translation (NAT).
A firewall product that runs NAT receives packets for one IP address, and translates the headers of the packet to send the packet to a second IP address. In environments with firewalls employing NAT, avoid configurations involving complex protocols in which IP addresses are embedded in the body of the IP packet, such as Java RMI or IIOP. These IP addresses are not translated, making the packet useless.
- Avoids the DMZ protocol switch.
The Web server sends HTTP requests to Application Servers behind firewalls. It is simplest to open an HTTP port in the firewall to let the requests through. Configurations that require switching to another protocol, such as IIOP, and opening firewall ports corresponding to the protocol, are less desirable. They are often more complex to set up, and the protocol switching overhead can impact performance.
- Allows an encrypted link between Web server and Application Server.
Configurations that support encryption of communication between the Web server and appserver reduce the risk that attackers are able to obtain secure information by sniffing packets sent between the Web server and Application Server. A performance penalty usually accompanies such encryption.
- Avoids a single point of failure. A point of failure exists when one process or machine depends on another process or machine. A single point of failure is especially undesirable because if the point fails, the whole system becomes unavailable. When comparing DMZ solutions, a single point of failure refers to a single point of failure between the Web server and Application Server. Various failover configurations can minimize downtime and possibly even prevent a failure. However, these configurations usually require additional hardware and administrative resources.
- Minimizes the number of firewall holes. Configurations that minimize the number of firewall ports are desirable because each additional firewall port leaves the firewall more vulnerable to attackers.
Some solutions are faster than others, in terms of the number of client requests they can process per unit of time. Some solutions require little or no maintenance after you establish them, while others require periodic administrative steps, such as stopping a server and starting it again after modifying resources that affect the configuration. To learn about the necessary maintenance for a topology, review the instructions for setting up and maintaining that topology. Of course, if you can automate the necessary administrative steps through command line clients and scripting, this might not concern you.
Multimachine topology concepts

Port number settings in WAS versions
Default coexistence settings for port numbers